In the latest SAP Patchday from February 2024, a number of security vulnerabilities have been closed. These vulnerabilities, ranging from code injections to cross-site scripting, pose significant risks to organizations using SAP software. February 2024 is characterized by two Hot News, six High, seven Medium and one Low security update.
The most important closed security gaps
One of the most serious vulnerabilities affects the SAP Business Client. An update has been released in versions 6.5, 7.0 and 7.70 to close vulnerabilities in the Google Chromium browser control. This vulnerability, which has a high severity of 10.0, could potentially cause serious security breaches if the update is not performed.
Furthermore, a code injection vulnerability was discovered in SAP ABA (Application Basis). Versions from 700 to 75I are affected. The severity of this vulnerability is 9.1, which indicates a risk of unauthorized code execution.
Another critical vulnerability affects SAP NetWeaver AS Java, more specifically the User Admin Application. Version 7.50 is susceptible to cross-site scripting attacks, which can lead to significant security threats. The severity of this vulnerability is rated 8.8.
In addition, an XXE vulnerability was identified in SAP NetWeaver AS Java (Guided Procedures). This vulnerability affects version 7.50 and has a high severity of 8.6.
A critical vulnerability affects the SAP CRM WebClient UI. Versions such as S4FND 102, S4FND 103 and others are vulnerable to cross-site scripting attacks with a severity of 7.6 (CVE-2024-22130).
Moderately serious security vulnerabilities of the SAP Patchday in February 2024
In February 2024, moderate security vulnerabilities were also identified in various SAP products that could potentially put companies at risk.
One of these concerns SAP Bank Account Management (BAM). A missing authorization check was discovered in versions SAP_FIN 618, SAP_FIN 730 and S4CORE 100 and 101. This vulnerability could allow attackers to access confidential bank account information or carry out unauthorized transactions.
Furthermore, a cross-site scripting (XSS) vulnerability was detected in SAP CRM (WebClient UI). Versions such as S4FND 102, S4FND 103, WEBCUIF 731 and others are affected. By exploiting this vulnerability, attackers could inject malicious code into the web application, causing data leaks or session hijacking.
In addition, an information disclosure vulnerability was discovered in SAP NetWeaver Application Server ABAP (SAP Kernel). Versions such as KERNEL 7.53, KERNEL 7.54 and others are affected. An attacker could extract confidential information from the system or initiate additional attacks if this vulnerability is exploited.
Urgent measures required
Organizations that use SAP products are strongly encouraged to do so:
- Apply patches: Immediate application of available patches and updates is critical to mitigate these vulnerabilities.
- Implement security measures: Additional security measures such as firewalls, intrusion detection systems and regular security audits should be implemented to strengthen system defenses.
- Stay informed: Continuously monitor security advisories from SAP and relevant cybersecurity authorities to stay informed of emerging threats.
We will be happy to help you install the updates. Simply contact us.
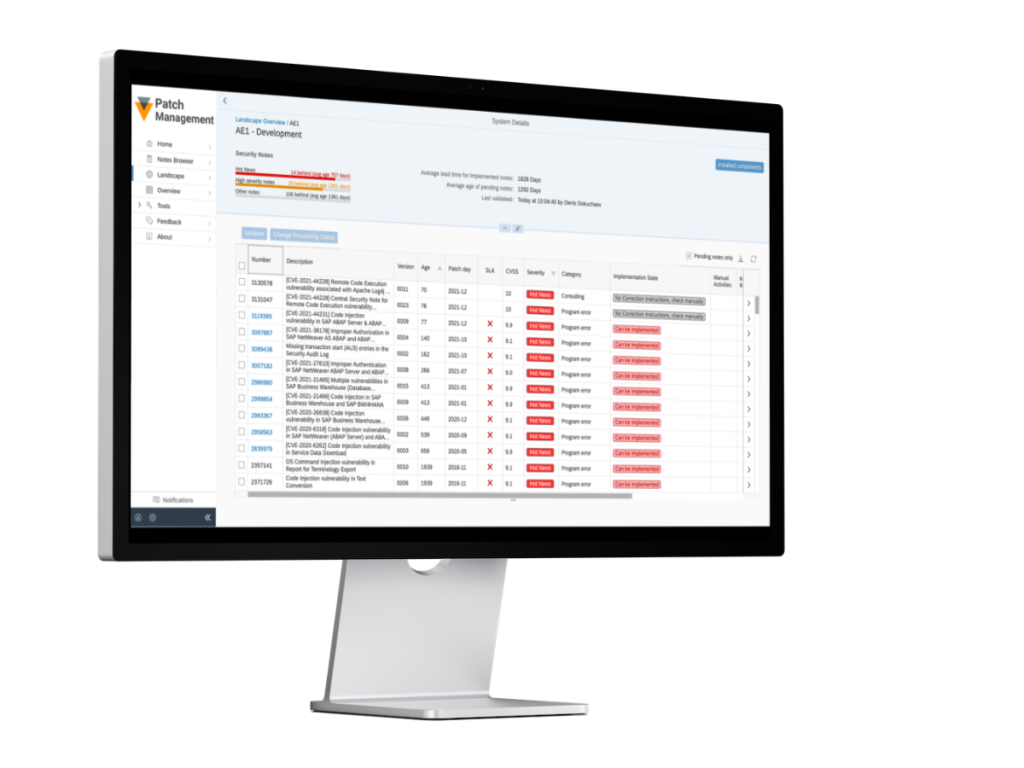
Use the SecurityBridge SAP Patch Management, to never miss an important update for your SAP system again!
Contact us to learn more about SecruityBridge!
Contact us!